
Microsoft fixes critical Teams account takeover vulnerability
A vulnerability found in Microsoft’s collaboration platform Teams could’ve allowed attackers to monitor and steal your company’s data by simply sending a crafted .GIF file in your Teams chat.
Security researchers at CyberArk discovered a subdomain takeover vulnerability in few Microsoft’s subdomains that are being used in the development of Microsoft Teams software.

See Also: Apple plans to fix a new iOS vulnerability in iPhone and iPad
How Teams fetch and display content to a user:
Every time a user opens teams app, Microsoft Teams client creates a temporary access token that is generated by Microsoft’s authorization and the authentication server – “login.microsoftonline[dot]com“
The generated token is called “skype token”, can also be seen as a cookie named “skypetoken_asm.”
This access token is used to display images and other media to a Teams user by fetching the content from Microsoft’s servers.
The Vulnerability Analysis
The vulnerability is related to how Microsoft Teams passes this authentication access token to image resources and how the Teams client uses this created token to display images shared with or by a user in the Teams app.
To ensure that the shared media is only restricted & displayed to the intended Teams recipients, Microsoft established cookies
called “authtoken” and “skypetoken_asm“
In a technical-writeup, CyberArk revealed that the contents present in the “authtoken” and “skypetoken_asm” cookies could be used to bypass
teams authentication mechanism and allow an attacker to send/read messages, create groups, add/remove users from groups, change permissions in groups, etc. by simply making API calls through Teams API interfaces.
How attackers could steal the data in the Teams app
The “authtoken” cookie contains an access token in the form of a JWT (https://en.wikipedia.org/wiki/JSON_Web_Token) and is set to be sent to only *.teams.microsoft.com (subdomains).
But in the research, CyberArk found out two of the following Microsoft’s subdomains vulnerable to subdomain takeover attacks:
1. aadsync-test.teams.microsoft[dot]com
2. data-dev.teams.microsoft[dot]com
“If an attacker can somehow force a user to visit the sub-domains that have been taken over, the victim’s browser will send this cookie to the attacker’s server and the attacker (after receiving the authtoken) can create a skype token. After doing all of this, the attacker can steal the victim’s Teams account data,” said CyberArk.
Exploiting the vulnerability by sending .GIF
In a POC video, CyberArk researchers showed how they leveraged these compromised subdomains to target a victim by simply attributing “src” to a .GIF image and sending it via Teams chat.
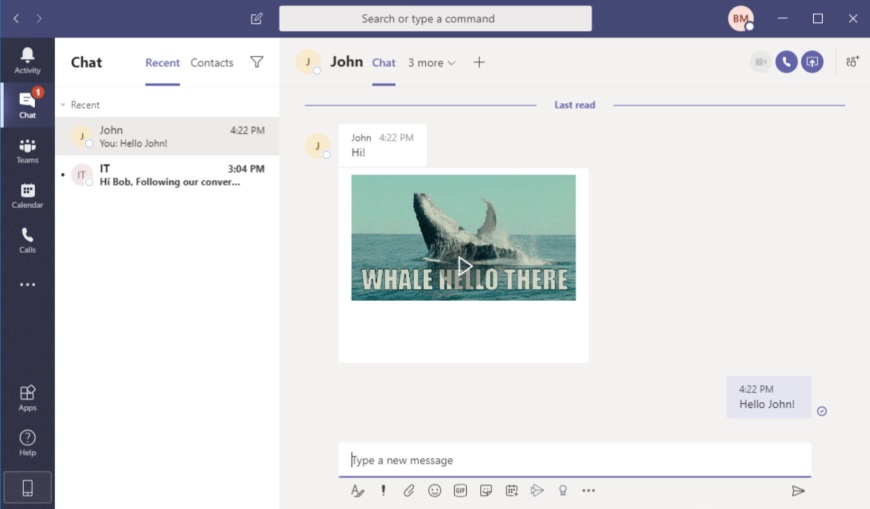
If a victim opens up the .GIF, it will allow an attacker to scrape all the Teams data.
“The victim will never know that they’ve been attacked, making the exploitation of this vulnerability stealthy and dangerous”, said researchers at CyberArk.
Worm-like Vulnerability
Researchers further described this vulnerability as similar to the worm virus that spreads automatically within a company’s network.
“The fact that the victim only needs to see the crafted message to be impacted is a nightmare from a security perspective. Every account that could have been impacted by this vulnerability could also be a spreading point to all other company accounts. The GIF could also be sent to groups (a.k.a Teams), which makes it even easier for an attacker to get control over users faster and with fewer steps,” the researchers also said.
See Also: Zoom App Vulnerability Allow Hackers To Steal Your Windows Password
To Mitigate this vulnerability
After discovering this account takeover vulnerability by combined efforts of CyberArk and Microsoft Security Research Center under Coordinated Vulnerability Disclose, Microsoft quickly removed the misconfigured DNS records of the two vulnerable subdomains that were exposed and could be taken over.
Besides, Microsoft has already pushed more mitigations to prevent similar kinds of flaws.
“Even if an attacker doesn’t gather much information from a Teams’ account, they could still use the account to traverse throughout an organization (just like a worm). Eventually, the attacker could access all the data from your organization’s Teams accounts – gathering confidential information, meetings and calenders information, competitive data, secrets, passwords, private information, business plans, etc.”, CyberArk concluded in the writeup.
