
Tupperware site hacked by cybercriminals to steal credit card details of customers
Tupperware[dot]com which sells kitchen and household products online recently fell victim to a cyberattack where cybercriminals hacked into their site and placed a malicious code within an image (.png) file using a form of steganography.
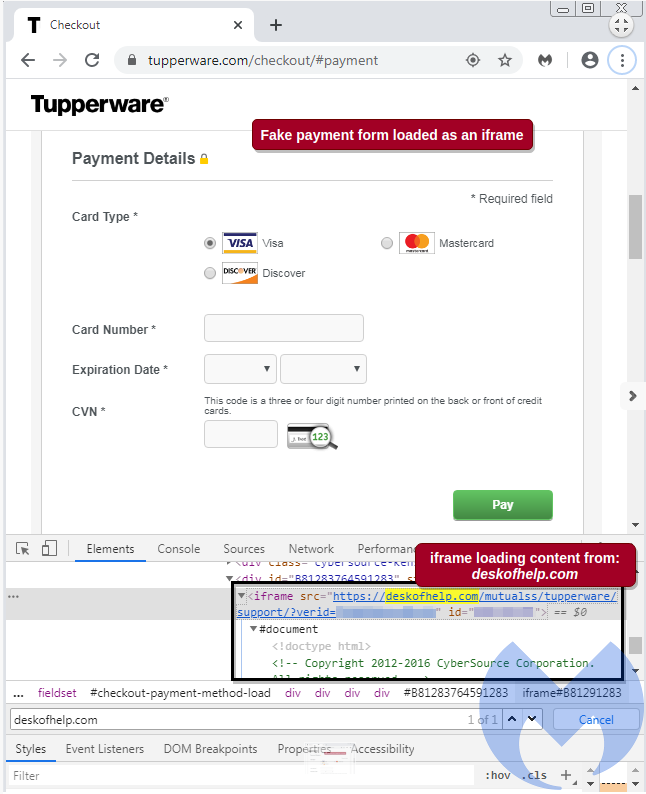
The malicious code present in that .png activated a fake payment form (in an iframe) during the checkout process. This form collected customer payment information via a credit card skimmer and passed that information to the cybercriminals.
On March 20, a security firm Malwarebytes discovered this rogue iframe container on the checkout page of tupperware[dot]com.
It was found that the iframe was loaded from a domain named deskofhelp[dot]com which is registered to elbadtoy@yandex[.]ru. This malicious domain is hosted on a server at 5.2.78[.]19 alongside a number of phishing domains.
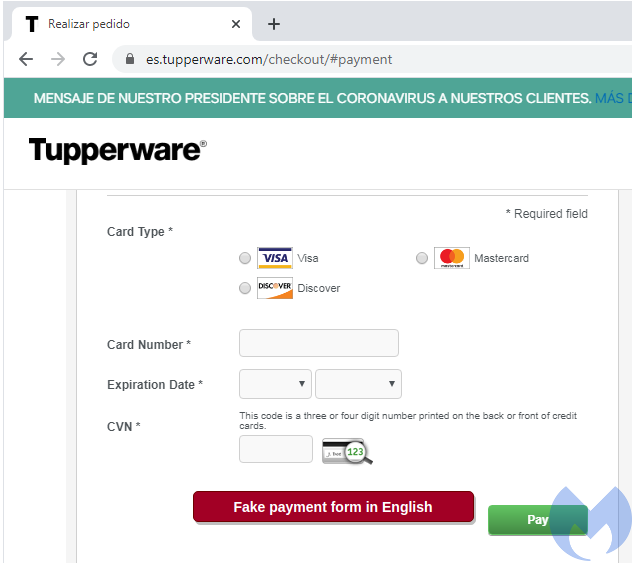
Malware researchers at Malwarebytes discovered this flaw in the integration of the credit card skimmer where attackers did not display that fake payment form in a local language. For example, the Spanish version of the Tupperware site displays a legitimate payment form written in Spanish, but the rogue payment form was still in English.
Twitter account for the Malwarebytes threat intelligence team confirmed that Tupperware has now removed the malicious code from its servers. Where the company has nothing to say about this incident.
Following publication of the blog, we noticed that the malicious PNG file has been removed. This will break the skimmer. ????
— MB Threat Intel (@MBThreatIntel) March 25, 2020
However, other artifacts remain present and a full security sweep will be necessary. pic.twitter.com/BAuByz8KsZ
If you have recently bought something from tupperware.com, it is advised that you should check your credit card statement, right now. Your following details may have been compromised: First name & last name, billing address, telephone numner, credit card number, credit card expiry date and CVV.

Read Also:
> Misconfigured Database of Virgin Media Exposes 900,000 Customers’ Information

One Reply to “Tupperware site hacked by cybercriminals to steal credit card details of customers”