
New wave of Adwind jRAT targeting co-operative banks in India
Co-operative banks in India have been recently targeted in an ongoing Adwind Java Remote Access Trojan (Adwind jRAT) campaign launched by cybercriminals to plant backdoors and steal sensitive data from banks.
Adwind, related to AlienSpy family, is a cross-platform RAT that has been targeting businesses since 2013.
Recently, an Anti-virus firm Quick Heal Security Labs observed a new wave of Adwind jRAT campaign targeting India’s co-operative banks since the starting of April 2020.
“This recent Java RAT campaign also starts with a spear-phishing email. In this case, the email claims to have originated from either Reserve Bank of India or a large banking organization within the country,” reads the report published by Seqrite last week.
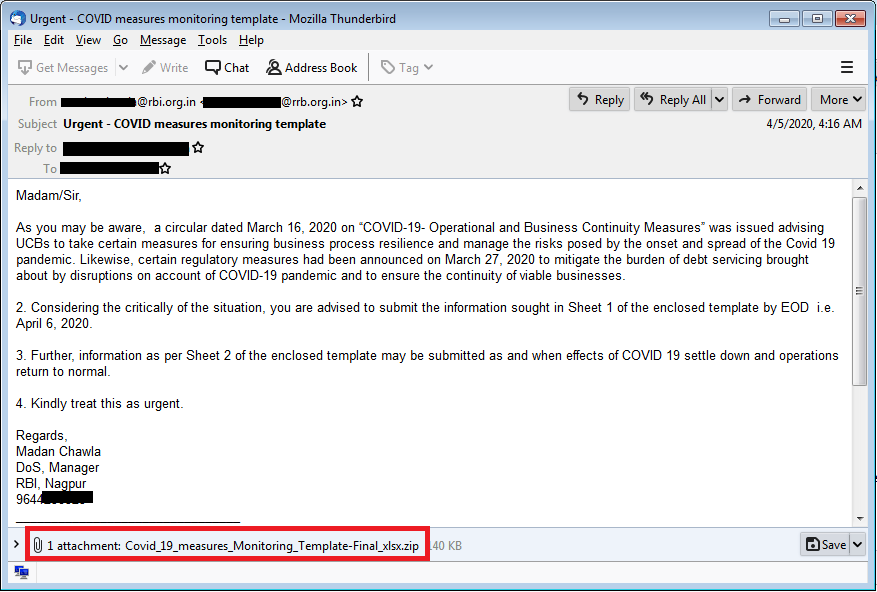
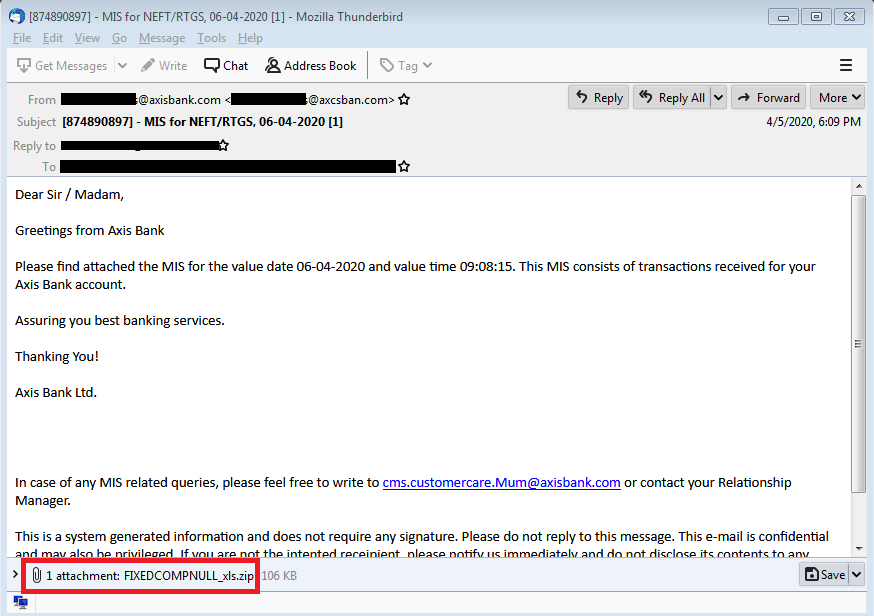
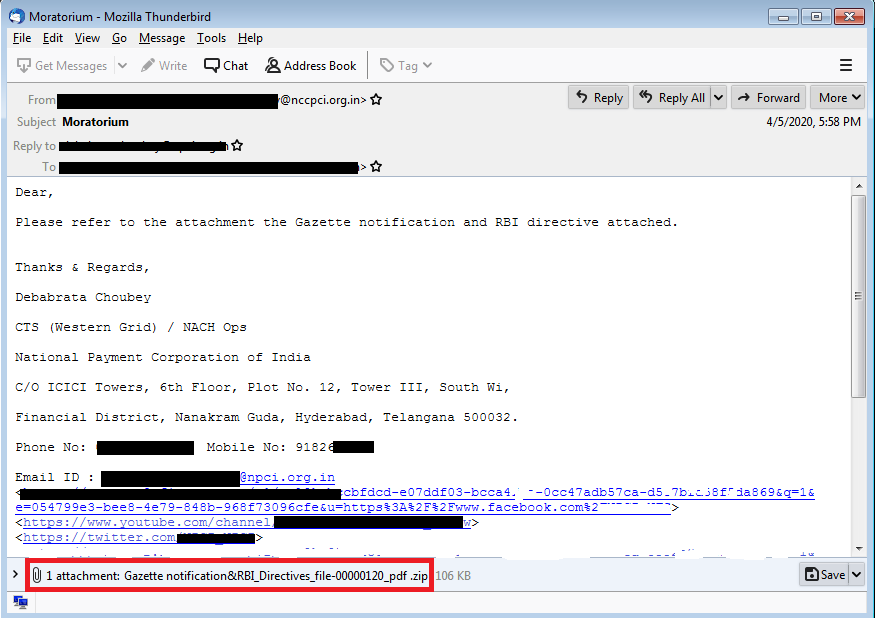
In a phishing email, cybercriminals are asking people to download a .zip that contains a malicious JAR file, which, upon execution “transforms into a Remote admin tool (JRat) which can perform various malicious activities such as keylogging, capturing screenshots, downloading additional payloads, and getting user information”.
“The name of JAR is impersonated to PDF, xls or xlsx. This impersonation lures the user to click on this JAR file resulting in the execution of Java RAT,” said researchers at Seqrite.
Researchers deeply analyzed the samples of Adwind JRAT trojan and found out that it communicates with its Command and Control (C2) server on non-standard ports. In this case, Port 9045 was used.
“RAT has the functionality to terminate or restart the connection based on commands received from C2”.
Further in the technical analysis performed by the researchers, they observed that the Adwind RAT is capable of controlling the the victim’s desktop, mouse, and keyboard remotely. It can also take commands from C2 to perform actions such as startup manipulation, Screen/Scroll capture, and File manager operations.
The impact of this attack could affect banks in not only direct costs but also in many indirect aspects such as stolen data, financial fraud, larger attacks, downtimes, loss of reputation, and customer impact.
Quick Heal has also provided IOCs for this Adwind jRAT:
1) D7409C0389E68B76396F9C33E48AB72B
2) 09477F63366CF4B4A4599772012C9121
3) 8C5FFB7584370811AF61F81538816613
4) 01AB7192109411D0DEDFE265005CCDD9
5) 0CEACC58852ED15A5F55C435DB585B7DThis seems to be another addition to the coronavirus-themed phishing campaigns and attacks targeting organizations all over the world.
For example: phishing campaign using WHO’s name to distribute info-stealing malware, COVID-19 themed attacks on Healthcare, phishing email with a fake voicemail note by Microsoft, and many more.

