
StrandHogg 2.0 bug in Android allows hackers to completely hijack any device
A critical privilege escalation vulnerability was recently discovered in all versions Android OS (not including Android 10) that can allow hackers to hijack any android device by infecting it with malware.
Security researchers at Promon dubbed this bug as the “StrandHogg 2.0” vulnerability (CVE-2020-0096) that can allow real-file malware (malicious app) to display as a legitimate app in an Android device without the user’s knowledge.
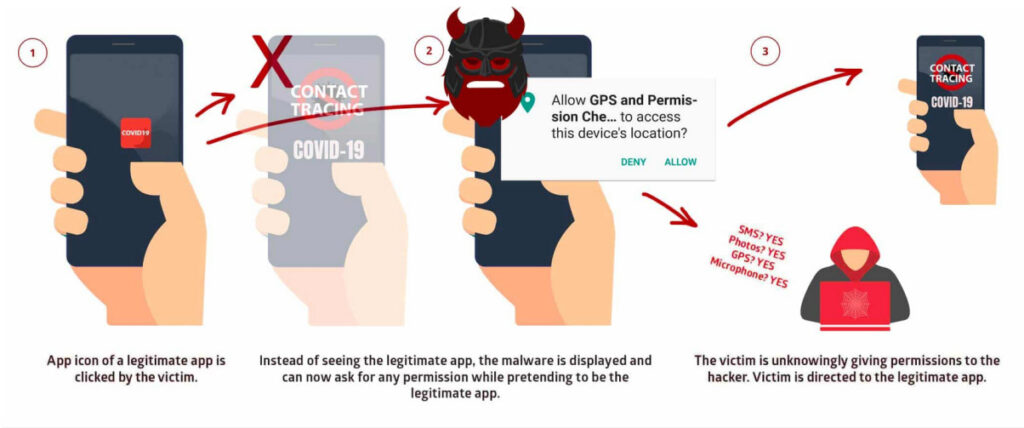
By exploiting this critical severity vulnerability, hackers can listen through the infected devices’ microphone, take photos through the camera, read and send SMS messages, get device location & GPS info., access contact list, and can even get access to phone logs.
The original StrandHogg vulnerability was discovered last year by the same researchers – John Høegh-Omdal, Caner Kaya, & Markus Ottensmann at Promon, but StrandHogg 2.0 allows hackers to launch a wider range of attacks by harvesting login credentials via a malicious app installed on a victim’s device.
See Also: New android malware EventBot targets over 200 banking and finance apps
The POC video posted by Researchers at Pomon:
“The attack can be designed to request permissions which would be natural for different targeted apps to request, in turn lowering suspicion from victims. Users are unaware that they are giving permission to the hacker and not the authentic app they believe they are using,” reads the report by Promon.
“Having learned from StrandHogg and subsequently evolved, StrandHogg 2.0 doesn’t exploit the Android control setting ‘TaskAffinity’, which hijacks Android’s multitasking feature and, as a result, leaves behind traceable markers,” reads the report published by Promon on Tuesday. “Strandhogg 2.0 is executed through reflection, allowing malicious apps to freely assume the identity of legitimate apps while also remaining completely hidden.”
The researchers reported this bug to Google in December and the tech giant released a patch in April 2020 and shared it with the device manufacturing companies, who have now started providing the security updates to their devices with a fixed security patch for Android versions 8.0, 8.1, and 9.
“With a significant proportion of Android users reported to still be running older versions of the OS, a large percentage of the global population is still at risk,” the researchers said.
According to data from Google, as of April 2020, 91.8% of Android active users worldwide are on version 9.0 or earlier: Pie (2018), Oreo (2017), Nougat (2016), Marshmallow (2015), Lollipop (2014), KitKat (2013), Jellybean (2012) and Ice Cream Sandwich (2011).

