
Microsoft Warns About Ongoing “Dudear” Campaigns That Deploy an Info-stealer
Security researchers at Microsoft have uncovered an ongoing phishing campaign launched by the ‘CHIMBORAZO’ group that is now using infected sites with the integrated CAPTCHA, to avoid automatic detection and deploy info-stealing Trojan called ‘GraceWire’ into the victim’s machines.
Read Also: Security researchers identify vulnerabilities in “Official Trump 2020” app
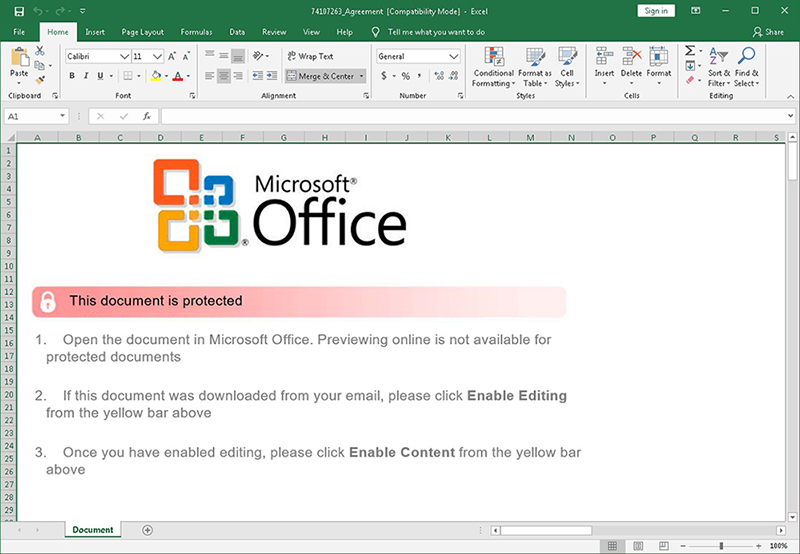
Back in January 2020, Dudear (aka TA505/SectorJ04/Evil Corp) targeted people all around the world with the HTML redirectors attached to their phishing emails. When opened, it resulted in downloading a malicious Excel file that infected the systems with the GraceWire Trojan.
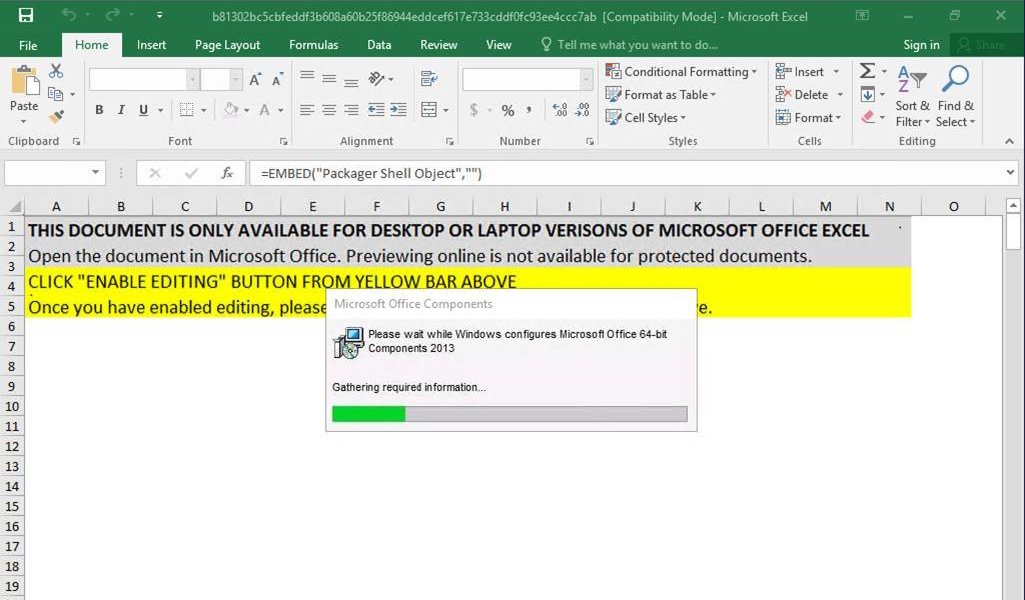
According to the researchers at Microsoft, it was the first time that Dudear used the HTML redirectors. The threat actors also used an IP traceback service to track the IP addresses of systems that downloaded the malicious Excel file.
Now, the group is using more evolving techniques and using CAPTCHA on the infected websites to evade the detection mechanisms.
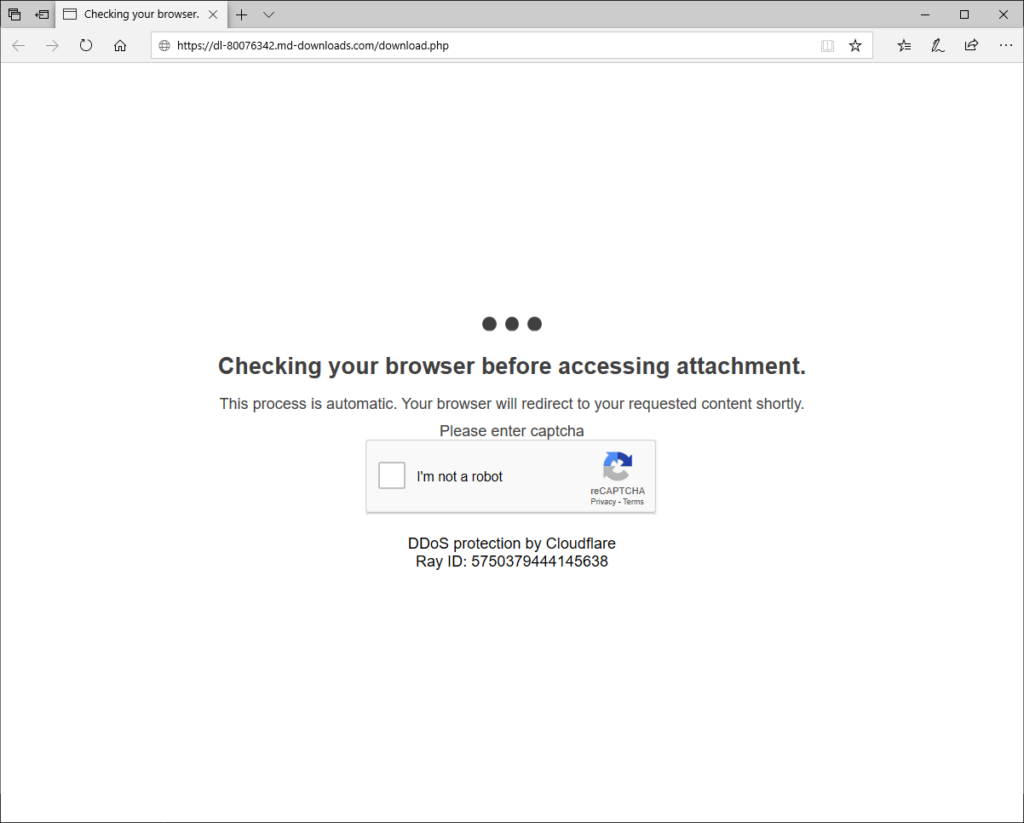
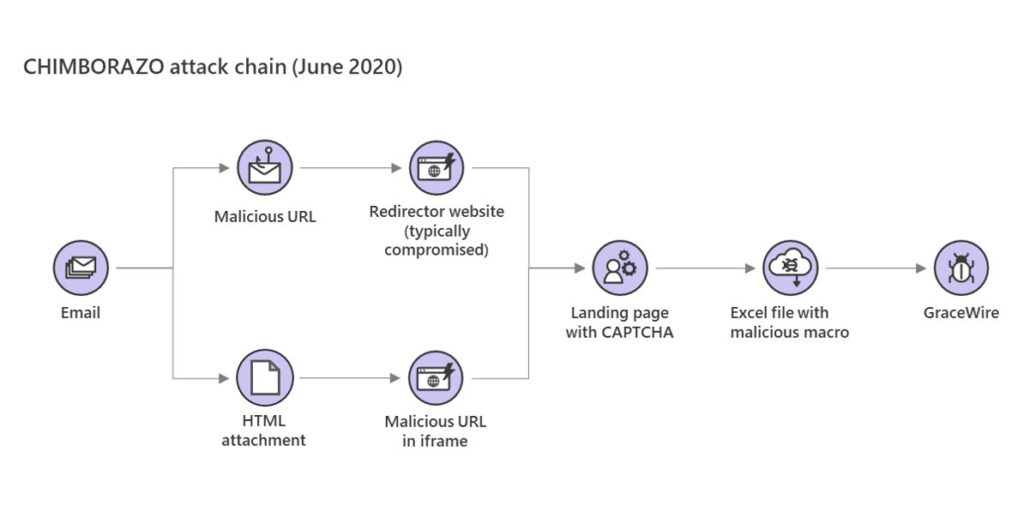
“We started observing these campaigns in early June, but we say them surge this week. The emails contain either a link to a redirector site (typically a compromised website) or an HTML attachment with a malicious URL in iframe. Both methods lead to the website with CAPTCHA,” said Microsoft in a tweet.
CHIMBORAZO, the group behind Dudear campaigns that deploy the info-stealing Trojan GraceWire, evolved their methods once again in constant pursuit of detection evasion. The group is now using websites with CAPTCHA to avoid automated analysis. pic.twitter.com/Kz3cdwYDd7
— Microsoft Security Intelligence (@MsftSecIntel) June 17, 2020
Microsoft Security Intelligence team has also released sample IOCs from this campaign:
SHA-256: c78cd6f7c29bb50d9a5cb2c4fd1be693ca988197ba5add87fb1b49ef7e91b04f (Excel file); 955dbc7e39627002a5a9ef1199257a980697ceabb14c24ad46a4067c6252439e (malware payload)
“Microsoft researchers continue to monitor CHIMBORAZO, its activities, and evolving methods,” also Microsoft tweeted.
TA505 hacking group is a Russian threat actor that has been active since 2014 and targeted many financial organizations in the United States and worldwide.
Between December 2018 and February 2019, the financially-motivated threat acting group was also seen targeting institutions in Chile, India, Italy, Malawi, Pakistan, and South Korea, by leveraging the Remote Manipulator System (RMS) backdoors.
Found this article interesting? Please share with your friends and colleagues. To receive more news updates, follow us on Facebook, Twitter and LinkedIn.

