Andhra Pradesh Police E-challan System Fixes Major Bug In apechallan.org
A security researcher discovered critical bug present in the Andra Pradesh Police E-challan System (apechallan[dot]org site) that exposed an unsecured database that contained private information of citizens as well as the source code of the entire site, QuickCyber has learned.
apechallan[dot]org was launched back in 2018 by the Andhra Pradesh government for the citizens to search and pay traffic fines online via e-Challan.
Read Also: ZEE5.com hacked: Hackers claim to have stolen data from the popular OTT platform
Last week, the security researcher and ethical hacker named Edwin Strut reached out to Quickcyber to tell us that he discovered vulnerabilities in the apechallan portal in 25th January 2020 and notified the site administrators about this issue 3 to 4 times but didn’t receive any response from them which left the e-Challan site vulnerable for five months.

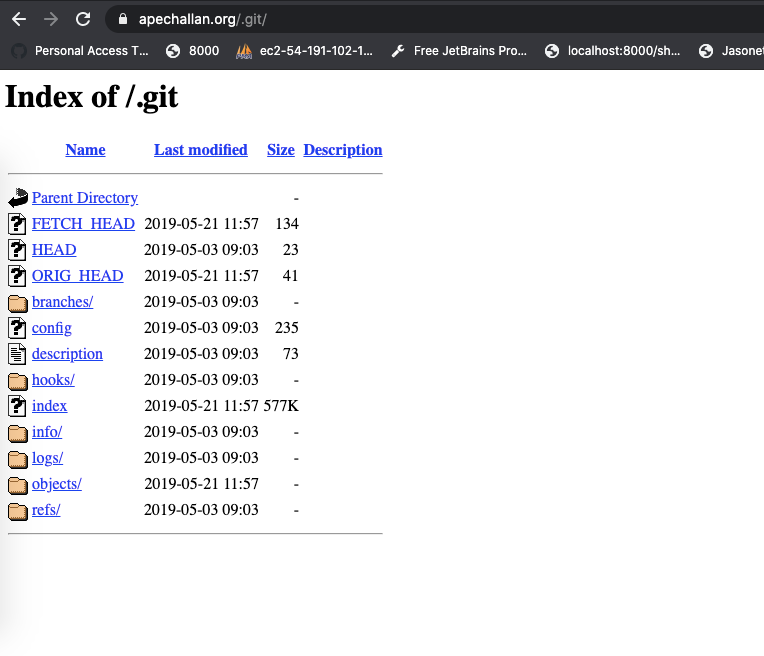
The exposed information contained code repository (.git) of the site along with the database of more than 29GB that contained sensitive information of the citizens including, their names, phone numbers, the status of paid/unpaid challans, charged amounts, etc.
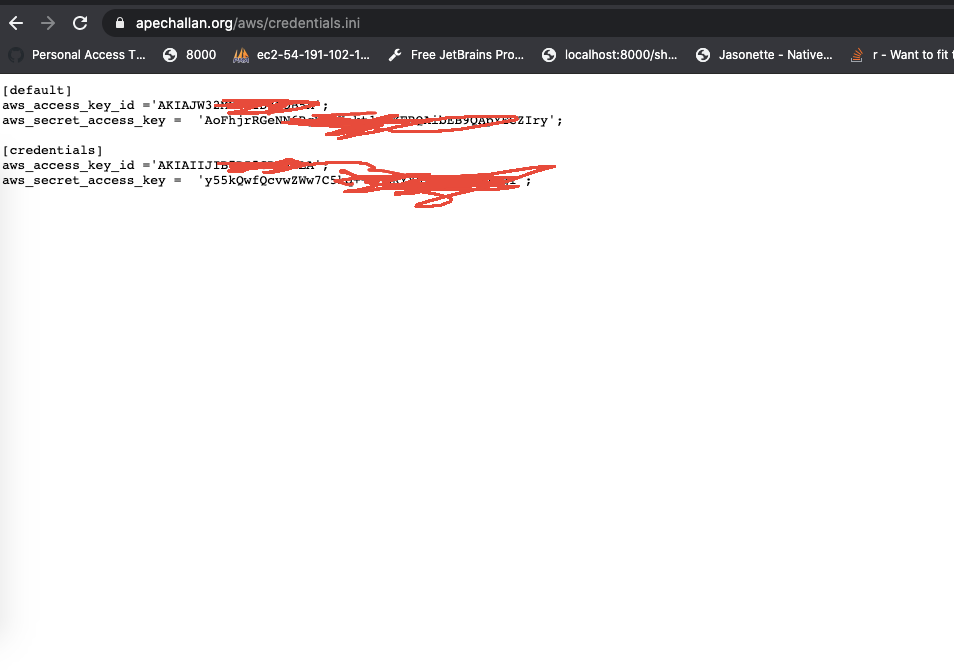
“In the code, database credentials were exposed, so I was able to access the database from my local IP, usually they have to block AWS RDS DB within IP Ranges,” Edwin told Quickcyber.
Edwin was able to obtain the unsecured database credentials by using a tool named git-dumper (a tool to dump a git repository from a website).
The apechallan site is developed by the third-party vendor Dataevolve Solutions Pvt. Ltd., Edwin also reached out to them and AP Police via E-mail and WhatsApp, but didn’t get any acknowledgment.

We suggested Edwin to report this vulnerability on CERT-in portal.
“After reporting to CERT-in (on 18th June 2020), the issue was fixed after two days (on 20th June),” Edwin told Quickcyber.
We also reached out to the admin of the apechallan[dot]org site seeking comments but couldn’t get anything yet.

