
Sophos fixes zero-day vulnerabilities in its XG Firewall products
Sophos recently released emergency patches for the SQL injection and malicious code execution vulnerabilities present in their XG Firewall products.
The vulnerabilities were reported by one of its customers regarding an “XG Firewall with a suspicious field value visible in the management interface”.
After receiving the report on 22nd April, Sophos commenced an investigation and found out that the incident was determined to be a zero-day attack against its physical and virtual XG Firewall products.
Yesterday, Sophos posted an advisory saying that “the attack used a previously unknown SQL injection vulnerability to gain access to exposed XG devices. It was designed to download payloads intended to exfiltrate XG Firewall-resident data.“
It was found that the hackers targeted XG Firewall devices that are configured with either the administration (HTTPS service) or their User Portal exposed to the WAN zone.
The company has now pushed a hotfix to XG Firewalls and notifying its both compromised and uncompromised customers on their firewall management interface.
- Notifying an uncompromised Firewall:
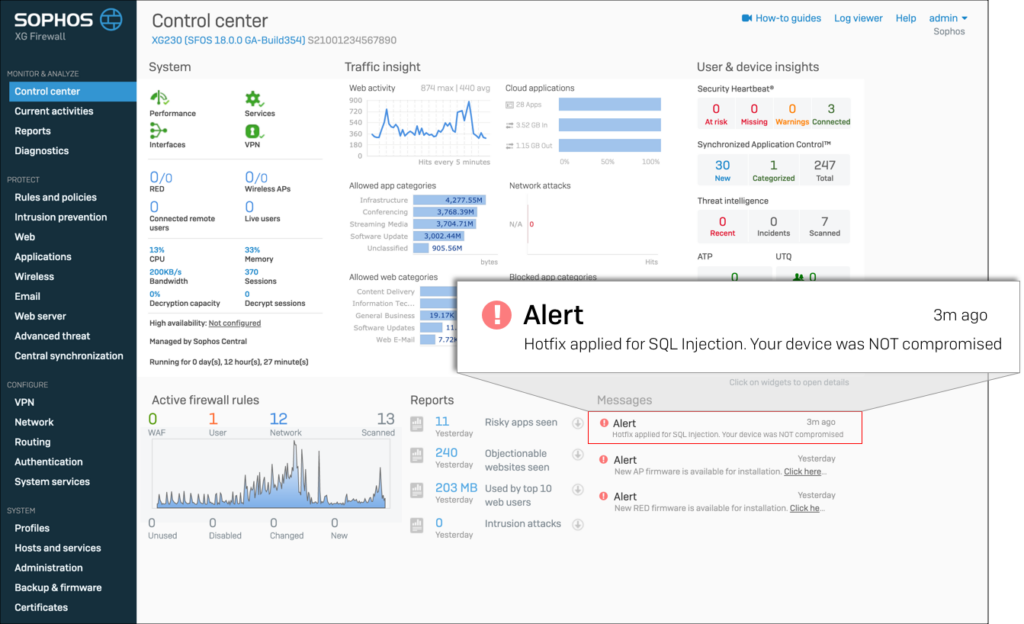
- Notifying a compromised Firewall:
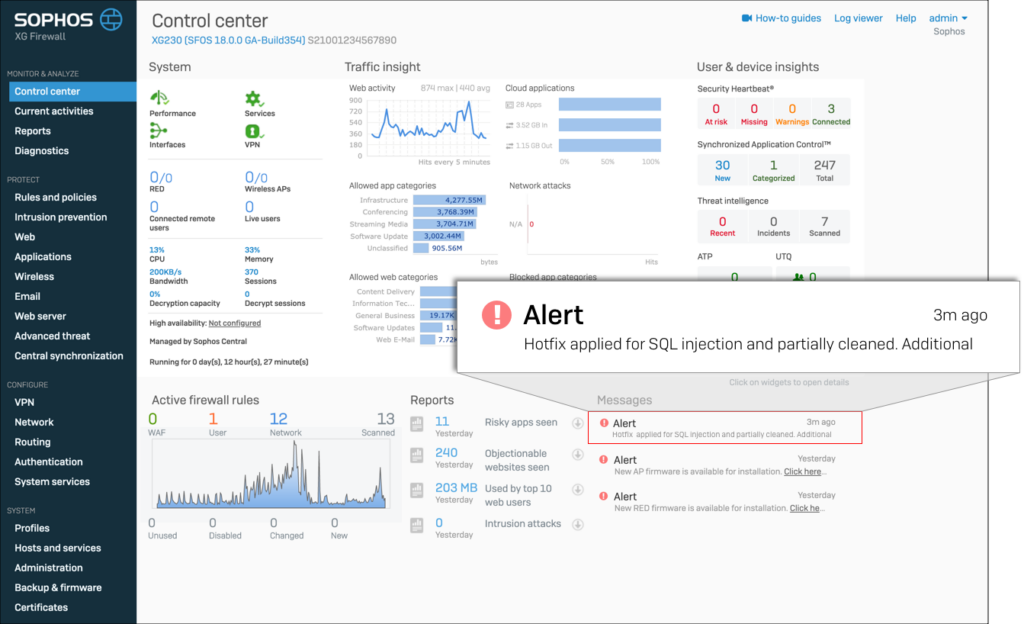
The Sophos advisory further recommends to take following additional steps to fully remediate the issue:
- Reset portal administrator and device administrator accounts
- Reboot the XG device(s)
- Reset passwords for all local user accounts
- Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused
Sophos also recommends its customers that are using older versions of XG Firewall/SFOS (virtual/physical) to protect themselves by upgrading to a supported version immediately.
Here are the supported versions of XG firewall firmware/SFOS : SFOS 17.1, 170.5, 18.0

